Daring Data-Theft is a video that explains the consequences of using Self-Signed certificates.
When customers use Self-Signed certificates for internal network encryption, they risk data theft. SecureNT Intranet SSL is superior to Self-Signed SSL certificates in several ways.
Self-Signed certificates are essentially certificates issued by individuals to themselves, with no external validation. These certificates can be issued quickly and valid for long periods, making them appealing for internal use.
One can issue such Certificates very easily (in seconds) and can be valid for long periods without any limit. Hence many users use Self-Signed SSL certificates for internal IPs or URLs.
However, this convenience comes at a great cost. Self-Signed certificates are extremely dangerous as the private key is stored in a PFX file with a weak or no password, making it easily accessible to those with bad intentions. This can lead to decryption of network traffic and data loss.
Furthermore, Self-Signed certificates pose additional issues. They cannot be revoked once compromised, and their continued use can lead users to ignore "Security Certificate Error" warnings, making the network vulnerable to malware and data loss. The private keys are not managed securely, leading to uncertainty and potential loss of important data or spoofed certificates.
Additionally, software developers often use Self-Signed certificates without documentation, which can end up in production systems, causing failures due to certificate expiry and unforeseen attacks. This can lead to irreparable damage to brand reputation and customer trust.
How is Intranet SSL better?
For public websites, one should use Certificates issued by public Certifying Authorities only. They use a minimum two-level "Certificate Chain of Trust", explained below.
For internal networks, one can set up an Internal Public Key Infrastructure (PKI) authority which can create a non-public Root CA Certificate, and use this Root CA certificate to issue SSL Certificates for internal use on Intranets. Here, there is a direct one-to-one relationship between the Root CA Certificate and the issued Certificate. But, this is one level of the hierarchy, and it is not enough.
We recommend creating an Intermediate CA Certificate using the Root CA Certificate; and using it to issue the SSL Certificates for internal use on Intranets. This is called a two-level "Certificate Chain of Trust."
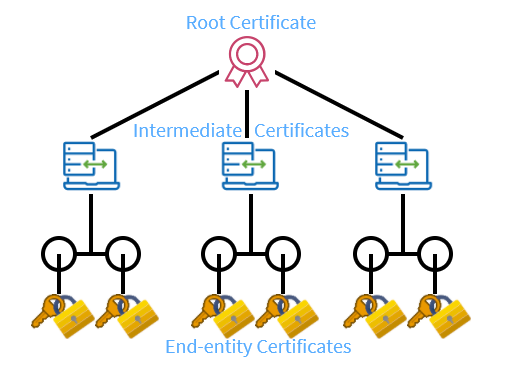
- Root CA Certificate - Private Key is used once to create an Intermediate CA Certificate. It is stored away from the PKI Infrastructure in a secret and secure place.
- Intermediate CA Certificate - Private Key is stored at PKI Infrastructure location to issue the End-entity SSL Certificates.
- End-entity SSL Certificate - This certificate requires both, Intermediate CA and Root CA Certificates to verify its identity and Trust Chain.
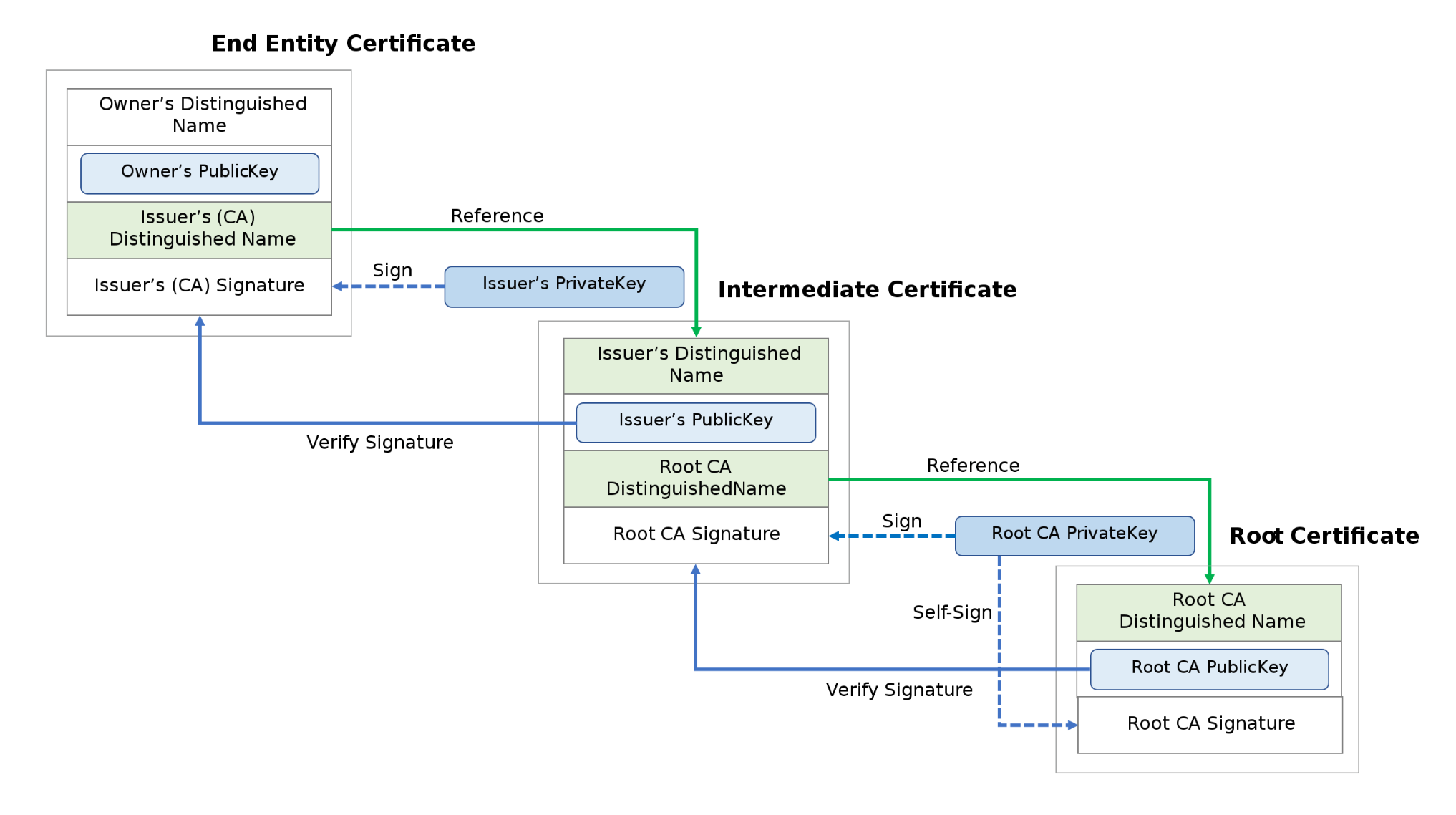
The roles of root certificate, intermediate certificate, and end-entity certificate as in the chain of trust.
Here, since the Private key of the Root CA Certificate is stored away securely, there is no risk of it going into the hands of a disgruntled employee or a hacker. All public Certifying Authorities also take this route of " Certificate Chain of Trust" because of its high security.
In the case of Self-Signed Certificates, there is no Trust Chain. The Private Key of the Root CA is stored within the PFX file. And these PFX files are stored on local PC or on Servers. They have no or weak passwords. If anyone with ill intentions gets to access these PFX files, he can manage to get the Private Key. He can use the Private Key to monitor the network traffic in unencrypted form on the internal network using sniffer tools. So, usage of Self-Signed SSL is fraught with severe data security risks.
But, setting up Internal PKI could be quite costly due to the requirement of highly skilled people. That’s where SecureNT Intranet SSL Certificates come in, to offer an easy solution. Just buy Certificates from us as and when required.
Copyright © 2026 Secure Network Traffic. All rights reserved. SecureNT is a registered trademark of Secure Network Traffic.