This question is crucial for CIOs of organizations, regardless of their size, with local area or wide area networks. These networks are used in various settings, including offices, branches, campuses, and factories.
Users access web applications like Office 365, email, service management, and sales automation, among others, either from their office network or remotely through a VPN. Some organizations also use Microsoft Active Directory and run high-end applications like ERP, CRM, and analytics, storing data in databases like Microsoft SQL, Oracle, and MySQL.
Their infrastructure often includes a mix of Windows and Linux servers hosting web applications, either on-premise or in data centers. However, we're not considering cases where vendors provide secure hosting, such as Office 365 or Salesforce. Instead, we focus on users accessing web applications hosted on on-premise or data-center servers over the LAN/WAN or VPN, connected via fiber, MPLS, or leased lines.
When users connect to these web applications, if the server lacks an SSL Certificate or uses a self-signed one, anyone can intercept internal network traffic and access sensitive information, including usernames, passwords, confidential files, and salary records. This "anyone" could be a disgruntled employee, IT service engineer, or even a hacker who gained unauthorized access to the internal network.
When working remotely through a VPN to access the office network, encrypting data is crucial to prevent hackers from obtaining sensitive information, especially from non-technical users who might unwittingly compromise their credentials.
Additionally, IoT devices that run local web services without direct internet access require secure access to those services using an SSL certificate. This need arises in scenarios where you:
- Use web applications on the intranet
- Allow employees to access the office network via a VPN (especially if the connection is not encrypted)
- Rely on local web services over HTTP connections
- Utilize Microsoft LDAP servers or SQL databases
- Self-sign SSL certificates
But I already use a Self-Signed Certificate which does the same things!
You might say that a self-signed certificate is enough to protect you with encryption, but is it? Think again.
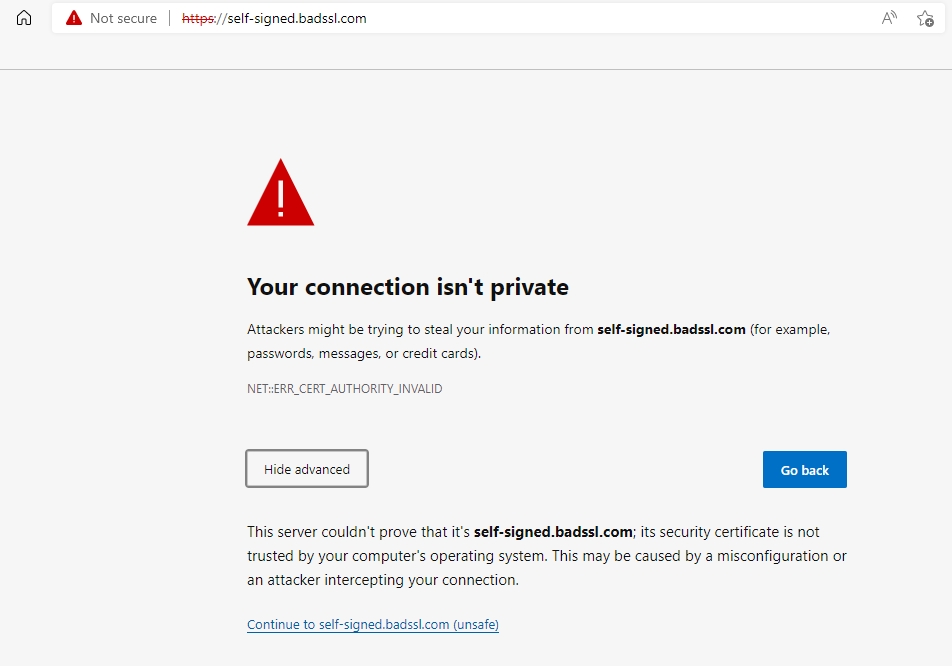
The PFX file containing the Self-signed certificate is stored somewhere on the internal network. Most of the time, such PFX files do not have a password or have extremely weak passwords like abc@123. If an unauthorized user gets access to it, he can use the Private Key stored inside the PFX file to decrypt the network traffic.
In most organizations, PFX files are not stored in a secure place, away from the internal network. They are casually created by the administrators and are routinely shared with users.
Because of the above reasons, it is prudent to use Intranet SSL/TLS Certificates on the internal servers.
Can't I set up my Private Certifying Authority ?
Yes. But it's very costly, requiring massive infrastructure and highly skilled personnel. Even large-size corporates find it prohibitively expensive. So, this option is almost non-existent for most organizations.
Large corporates using Windows Servers use Microsoft Active Directory Certificate Service (ADCS) to set up their own Certifying Authority and issue SSL Certificates. But, this route is for top corporates only. Please read this and this article to understand the difficulties.
I already have SSL certificates for my websites. Can't I use them for Internal Networks too ?
No. CA/Browser Forum does not allow Public CA's like DigiCert, GlobalSign, EnTrust, Sectigo, Let's Encrypt, etc. to issue SSL Certificates to IP Addresses (Internal or Public), Server Names, Local Hosts, or internal Web URLs.
Some of these CAs issue Intranet SSL Certificates using non-Public Root Certificates but at a high price. We take a similar approach but offer them at an affordable price.
Copyright © 2025 Secure Network Traffic. All rights reserved. SecureNT is a registered trademark of Secure Network Traffic.