People in charge of Cyber Security give great importance to the security of public-facing websites and applications. A lot of money is spent on Firewall, Traffic Analysis, Malware Detection, Network Access Control, etc. And very little attention is paid to the security of the internal network, where most valuable information is stored.
They assume that the internal network is quite secure. Why? Because everyone on the internal network is a trusted person. To a large extent, this is true as well. But what if an unhappy employee is there among the trusted people? What if a hacker gets access to an internal network? Since most important information is stored on the internal network, many unpleasant things can happen once someone with ill intent is inside.
Since Work from Home (WFH) has become routine, this issue has assumed great importance. Hackers can easily steal WFH credentials from unsuspecting non-tech-savvy employees. And once in, they can copy/manipulate crucial information before their unauthorized access is even noticed by the Cyber Security team.
The question is how to prevent such incidents.
By ensuring that all internal network traffic is encrypted. All internal servers hosting browser-based applications like SAP, SAS, PeopleSoft, Payroll, HRMS, CRM, and Service Desk management applications should have SSL/TLS certificates. If done, all the internal network traffic is encrypted, making it difficult even for the most experienced hacker to steal information.
If you are working from home on Office Servers using Virtual Private Networks (VPN) then it is recommended that network traffic is encrypted using SSL Certificates. If data on the Intranet networks applications is flowing in plain text (i.e., unencrypted), then any snooper can easily access confidential data using simple snooping tools. Also, it will allow hackers to view internal communication and other important information, such as usernames, passwords, confidential files, and human resource data.
Some people use Self-Signed Certificates to encrypt the data on the internal network. Let’s see what happens in such situations.
Have you seen this Security Error on your internal network, and ignored it?
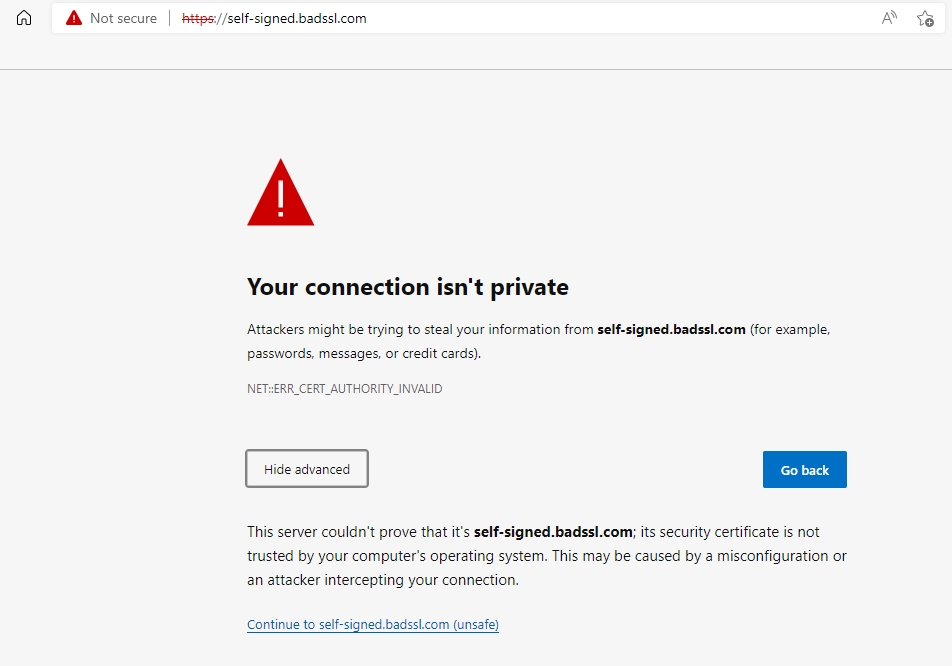
This error is seen when one uses Self-Signed Certificates to encrypt the data. One can issue such Certificates very easily in seconds and they could be valid for very long periods without any limit. Hence many users use Self-signed SSL certificates on internal IPs or URLs.
While it is cheap and easy one should keep in mind the disadvantages. The main problem is that once created the private key is not stored separately in a secure place. It is usually stored in a PFX file along with the certificate with a weak or no password. And they are usually found on file servers or local PCs. Any person with a bad intention can use the private key stored inside the PFX file to decrypt the network traffic. So, it’s very risky to use self-signed certificates.
Issues with Self-signed Certificates are covered in detail in this article.
Is there a solution? YES!!! SecureNT Intranet SSL Certificate
Our SecureNT Intranet Certificates are issued to an Intranet URL, a server name, or a private/public IP address. They are useful for ensuring Secure (HTTPS) network traffic for web-based applications, data traffic from LAN and WAN users, Server to Server communication, VPN Networks for Work from Home users, and Internal Email traffic using Secure POP3/IMAP & SMTP protocols.
No need to set up in-house PKI Infrastructure; or use Self-Signed Certificates
Even software developers requiring HTTPS connections to web services can use these certificates. If the internal network traffic is not encrypted, then this would allow attackers to view the internal communication on the network, thus increasing the chances of prying on confidential usernames, passwords, confidential files, human resource data, etc.
Using our service, you can get Intranet SSL/TLS certificates without the need to run your own in-house CA or usage of self-signed certificates.
Also, one can issue certificates with options that would otherwise not be permitted under public hierarchies, including the use of the SHA1 Hash Algorithm and longer-duration certificates.
